
Telcos says a new safeguard will help prevent sim card hijacking - where someone contacts Spark, Vodafone or 2degrees, pretending to be you, then takes control of your mobile phone number - then uses it to aid identity theft or fraud.
The Herald has been highlighting the problem of sim card hijacking since 2019. In March 2020, Cert NZ director Rob Pope said around 10 Kiwis had been victims of the crime of the past year.
Pope warned the public that because it gives a hacker such pervasive control over your life, the average loss has been large: about $30,000 per victim. People lose access to their own phone number just as they need it most as a fraudster uses it to loot their bank account.
It's often a nightmare to unwind.
In May 2020, police issued an expanded warning, saying a spate of sim card hijackings had cost 30 New Zealanders more than $1 million, including an Otago real estate agent who lost $120,000 after his Westpac password was changed via confirmation by txt.
And just last month, the owner of a Thai restaurant in Ellerslie lost her life-savings to an apparent sim card hijack.
Telcos tightened procedures. For example, Spark said customers had to visit one of its retail stores and show identification before a sim card, and its number, could be swapped to a new owner.
But Spark, Vodafone and 2degrees all said their anti-fraud efforts were hampered by well-intended number-porting rules, aimed at tamping-down "win-back" marketing, that prevented them from contacting a person who had quit their service.
That is about to change, says the Telecommunications Forum (TCF), an industry group that includes all the large telecommunications providers.
From tomorrow, people who switch mobile providers and want to keep their phone number – a process called number porting – will receive a dedicated SMS text message to help prevent fraudsters, the TCF says.
The text will alert the consumer that their mobile provider has received a request to port their phone number. If they did not request the port, it may be fraudulent and the consumer can then take action to alert their mobile provider and bank.
It will read:
"We're processing a request to move your mobile number to another provider. If you DID NOT request this, please contact your mobile provider and bank IMMEDIATELY as an unauthorised mobile transfer may leave you vulnerable to serious fraud. Do not reply to this text."
A more advanced SMS solution is under development and is expected to be rolled out in October. Once implemented, customers who have had a porting request on their account will receive an SMS from their provider to which they will need to reply "YES" for the number porting process to occur, the TCF says.
"Number porting" - or letting customers keep the same number when they move to a new mobile provider - was introduced in 2007 in a bid to goose competition.
"Consumers have benefitted greatly as it has made it easier for them to switch providers and get better deals," TCF comms director Andrew Pirie says.
"However, as an industry we've become concerned recently about the potential for fraudsters to exploit the process. With these new security measures, we aim to add another layer of protection for our customers."
Number porting fraud is relatively new and uncommon in New Zealand, but it can have a devastating impact on the victim, the TCF says.
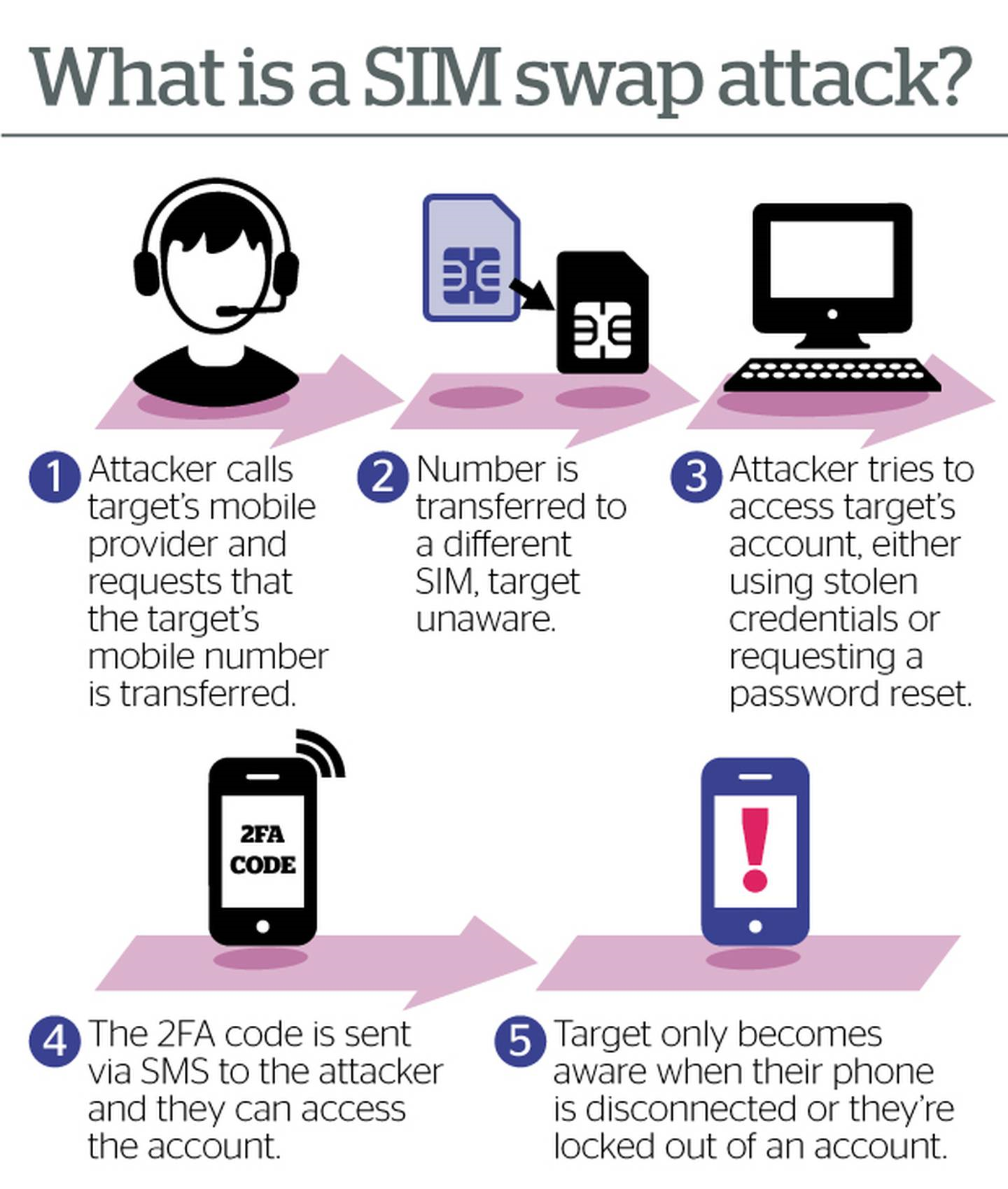
A fraudster obtains personal information about the victim, such as their name, mobile number and account details, often gained from hacking into an individual's email account.
The fraudster then requests to have the victim's mobile number transferred to the fraudster's sim card on a new provider. If successful, the fraudster will receive all the voice calls and text messages intended for the victim.
Typically, this occurs after a fraudster has managed to gain access to a customer's bank account – either by hacking or illegally obtaining the customer's banking password.
Armed with this information, the fraudster can then take advantage of a security process called "two-factor authenticatio"' which is where a service, like online banking, uses a text message to send a unique code that the customer needs to provide when logging in or when confirming a banking transaction. This means the fraudster can request a funds transfer from the victim's bank account and can use the SMS code to confirm the transfer.
Take your Radio, Podcasts and Music with you









